IT Security – Follow the Germans!
- by Florian Schütz

Information is an essential value for companies and must therefore be adequately protected. Reliable functioning information processing as well as the associated technology are essential for the maintenance of the operation. Inadequately protected information is a frequently underestimated risk factor that can even be existence-threatening.
Sure, we are talking about networks and communication, IT systems and applications. Tech stuff. But don´t be fooled, IT Security is not simply a technology issue, it´s a wider topic. IT security also includes the employees of a company, or organizational processes. Who has access to your office? Do you give guests access to your office Wi-Fi? What kind of apps can you download on your office mobile phone? The safety of the operating environment, the adequate training of the employees, the reliability of services, the proper handling of information to be protected and many other important aspects must under no circumstances be neglected. And last but not least, the management must provide adequate staffing and budget. Deficiencies in information security can lead to significant problems.
- Loss of availability
- Loss of confidentiality of information
- Loss of integrity (correctness of information)
But as IT security is a wide field, how to address all issues? How to cover all these different topics? The answer is to utilize an IT security framework. In software development, the usage of existing frameworks is pretty normal. No one - without a very good reason- would start a new project from scratch. You take existing frameworks and build your application on top. A framework is a kind of pre-programming, where various functions and elements are already included and do not have to be reprogrammed every time. The software developer can access these elements within the framework, which makes programming easier, more structured and saves a lot of time. Effective data security does the same. Take an IT security framework to provide a blueprint that identifies and classifies potential security risks across all enterprise computing assets and defines data security policies. The outcome can be used as a guide to prioritize necessary investments. After understanding the advantages of using an IT security framework the question arises what the best solution might be?
Follow the Germans
In my opinion the best theoretical basis of a security concept is at the moment the IT-Grundschutz security framework developed by the German Federal Office for Information Security of Germany, the BSI - Bundesamt für Sicherheit in der Informationstechnik. The BSI is first and foremost the central IT security service provider for the federal government in Germany. However, the BSI also offers its services to private and commercial users and providers of information technology.
As a sound and sustainable management system for information security, IT-Grundschutz covers technical, organizational, infrastructural and personnel aspects in equal measure. With its broad foundation, IT-Grundschutz offers a systematic approach to information security that is compatible to ISO/IEC 27001.
IT-Grundschutz is based on clustering all topics covering aspects of security into modules, which are divided into process-oriented and system- oriented modules and grouped together in a layer model based on matching topics.
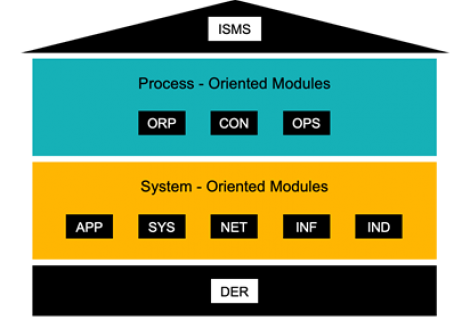
The process- oriented modules are grouped into the following layers:
- ISMS - Information Security Management Systems
- ORP - Organization and Personnel
- CON - Concepts
- OPS - Operations
- DER - Detection and Reaction
The system-oriented modules are grouped into the following layers:
- INF - Infrastructure
- NET - Networks and Communication
- SYS - IT Systems
- APP - Applications
- IND - Industrial IT (not needed for websms|)
The different modules of the IT-Grundschutz Compendium contain security recommendations on a wide variety of topics. Detailed advice and safeguards in the implementation guidelines for the IT-Grundschutz modules make it easier for information security officers to apply information security in their day-to-day work. You can find more information here:
https://www.bsi.bund.de/EN/Topics/ITGrundschutz/itgrundschutz_node.html
